OFAC Sanctions: IRGC-Affiliated Cyber Actors

On 14 September, the US Treasury’s Office of Foreign Assets Control (OFAC) released a fresh round of cyber and crypto-related sanctions. These new designations targeted Islamic Revolutionary Guard Corps (IRGC) affiliates involved in a ransomware campaign against the US and other nations. These activities, according to OFAC, have been ongoing since at least 2020.
In total ten individuals and two entities were sanctioned for their roles in conducting malicious cyber acts - all Iran nationals and Iran-based organisations.
The IRGC-affiliated group reportedly exploited software vulnerabilities and engaged in unauthorised computer access, data exfiltration, and other malicious cyber activities. Some of their malicious cyber activity can be partially attributable to several named intrusion sets, such as “APT 35,” “Charming Kitten,” “Nemesis Kitten,” “Phosphorus,” and “Tunnel Vision.”
Infrastructure Targets
As per the US Treasury, the IRGC-affiliated group targeted a number of key infrastructure assets in the US:
- In February 2021 the group targeted a New Jersey municipality through a computer network using a specific Fortinet vulnerability.
- In March and April 2021, it launched a set of encryption activities by compromising networks, activating Microsoft BitLocker without authorisation, and holding the decryption keys for ransom.
- In June 2021, the group gained unauthorised access to supervisory control and data acquisition systems associated with a US-based children’s hospital.
- From June to August 2021, the group targeted a wide range of US-based victims, including transportation providers, healthcare practices, emergency service providers, and educational institutions.
- From September 2021 until now, the group gained unauthorised access to victim networks by exploiting Microsoft Exchange and related ProxyShell vulnerabilities, including an incident in October 2021 when they compromised the network of an electric utility company.
Sanctioned Crypto Addresses
OFAC’s designation includes six Bitcoin addresses (with one mentioned twice in two separate profiles) as personal identifiers. These addresses are tied to two individuals connected to the IRGC affiliated group, according to OFAC. The addresses are as follows:
- 1H939dom7i4WDLCKyGbXUp3fs9CSTNRzgL
- bc1q3y5v2khlyvemcz042wl98dzflywr8ghglqws6s
- bc1qx3e2axj3wsfn0ndtvlwmkghmmgm4583nqg8ngk
- bc1qsxf77cvwcd6jv6j8d8j3uhh4g0xqw4meswmwuc
- bc1q9lvynkfpaw330uhqmunzdz6gmafsvapv7y3zty
- bc1qpaly5nm7pfka9v92d6qvl4fc2l9xzee8a6ys3s
All addresses have been added to Risktrail and to EthScamCheck. Profiles of the sanctioning event are also being prepared for Risktrail’s Sanctions Review section, for deeper insight on the activity, the perpetrators, and the underlying crypto assets.
Crypto HNWIs: who they are and how they made their wealth
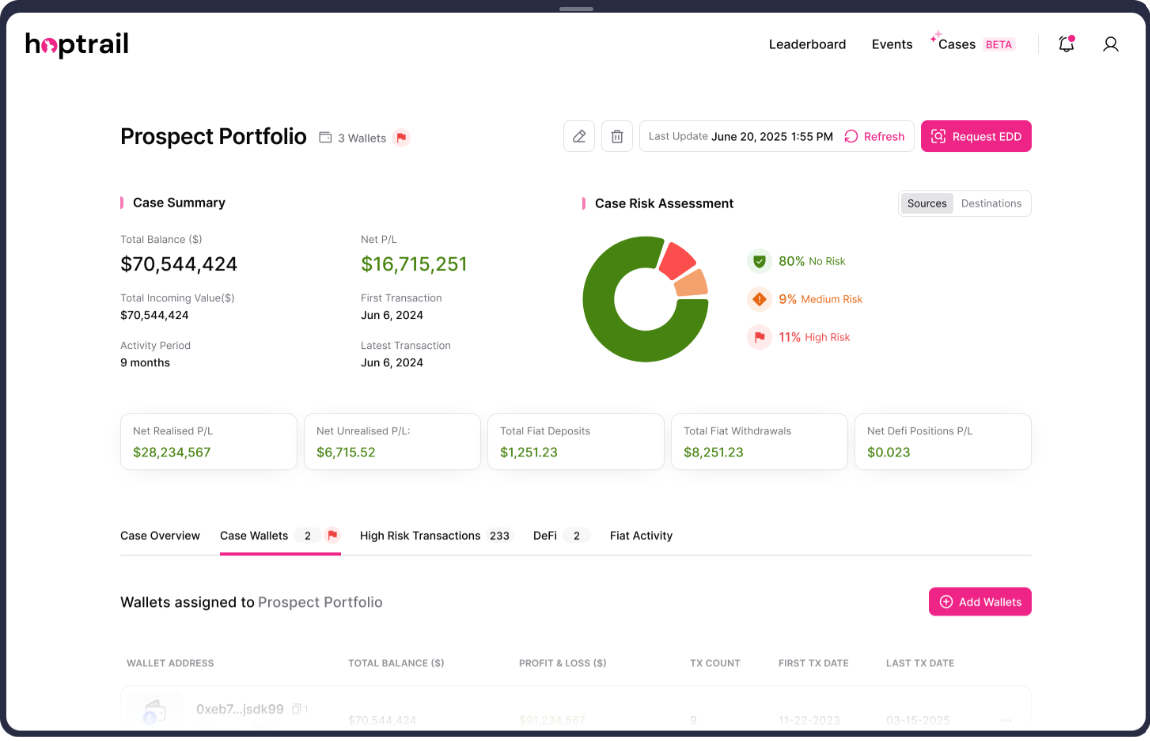
Cases: new source of wealth capabilities and upcoming features
Why we built Cases: A personal note on solving the crypto source of wealth headache
Subscribe to the Hoptrail newsletter
Sign up with your email address to get the latest insights from our crypto experts.
