Wintemute Hack: Vanity Affair

The deadline for the hacker to return the $160 million stolen this week from Wintermute has passed. The outside chance of a so-called white hat event, as hoped by Wintermute - one of the largest liquidity providers in the crypto space - has come and gone.
Wintermute has since confirmed it has sufficient reserves to continue operations; their CeFi holdings and their OTC operations were not affected. But it is no doubt damaging, particularly to a player with seemingly solid internal controls.
Immediate Aftermath
From very early on it was unlikely to be a white hat hacker. Data on the theft showed a series of rapid transfers, including the brazen movement of significant amounts of USDT, USDC, and DAI (approximately $111.9 million) from the hacker’s wallet to Curve, the popular DeFi protocol. Among other things, Curve allows users to earn interest by depositing funds into liquidity pools.
And that is exactly what the hacker did. You can see the transfer here. They are now earning between 0.3 - 0.7% APY on the stolen goods. Quite a staggering move!
Some experts have noted that the hacker was sophisticated enough to create a contract and deposit funds into a DeFi pool fast enough to avoid blacklisting. In theory, because of this, the hacker could begin withdrawing unstaked funds from Curve without detection.
Profanity Vanity
Another interesting aspect is Wintermute’s use of vanity addresses, which they reportedly generated via the Profanity service. Vanity addresses allow you to prefix characters in your wallet address. Sometimes, they are used for marketing; other times its just for fun. For example, this Bitcoin address is a palindrome:
- 1234mNnAPb8YnCsbacaNhB4BqwxB4U4321
This one was probably made by someone called Leonhard:
- 11111111LeonhardEu1er111126nxjP
In the Ethereum world, vanity addresses can be used to save on gas (transaction) fees. On blockchains, incremental gains in efficiency can lead to big cost reductions. Its a relatively obscure technique but using an address with more zero bytes (i.e. more zeros, which lowers so-called hamming weight) allows users to save on types of transactions.
And this is exactly what Wintermute did. Look at their main wallets:
- 0x0000006daea1723962647b7e189d311d757Fb793
- 0x000002Cba8DfB0a86A47a415592835E17fac080a
The issue was that the service they used to generate these addresses reportedly contained a bug. A bug that was disclosed recently (apparently by decentralised exchange 1inch) and exploited this week to enable the theft of funds from Wintermute’s DeFi wallets.
There is a wider debate to be had as to whether it was right for 1inch to publicise the bug, as profanity addresses would then become a target for hackers.
Speculation and Outcome
There is still wide speculation about these series of events, and the exact details remain unclear. But the Profanity bug has been talked about by Wintermute’s CEO on Twitter.
Others have speculated that because of the lower amount of bits in the address, the private keys could have been brute forced within a month or two.
Whatever the precise series of events, the issue highlights the extent to which users are required to go in order to protect their funds.
Due to the hack, and as publicised by Hoptrail this week, Wintermute’s rating on our AML Leaderboards has fallen in the Services category, from 6th to 9th place with a score of 80.72.
Get in touch to find out more about our crypto AML Leaderboards and Profiles.
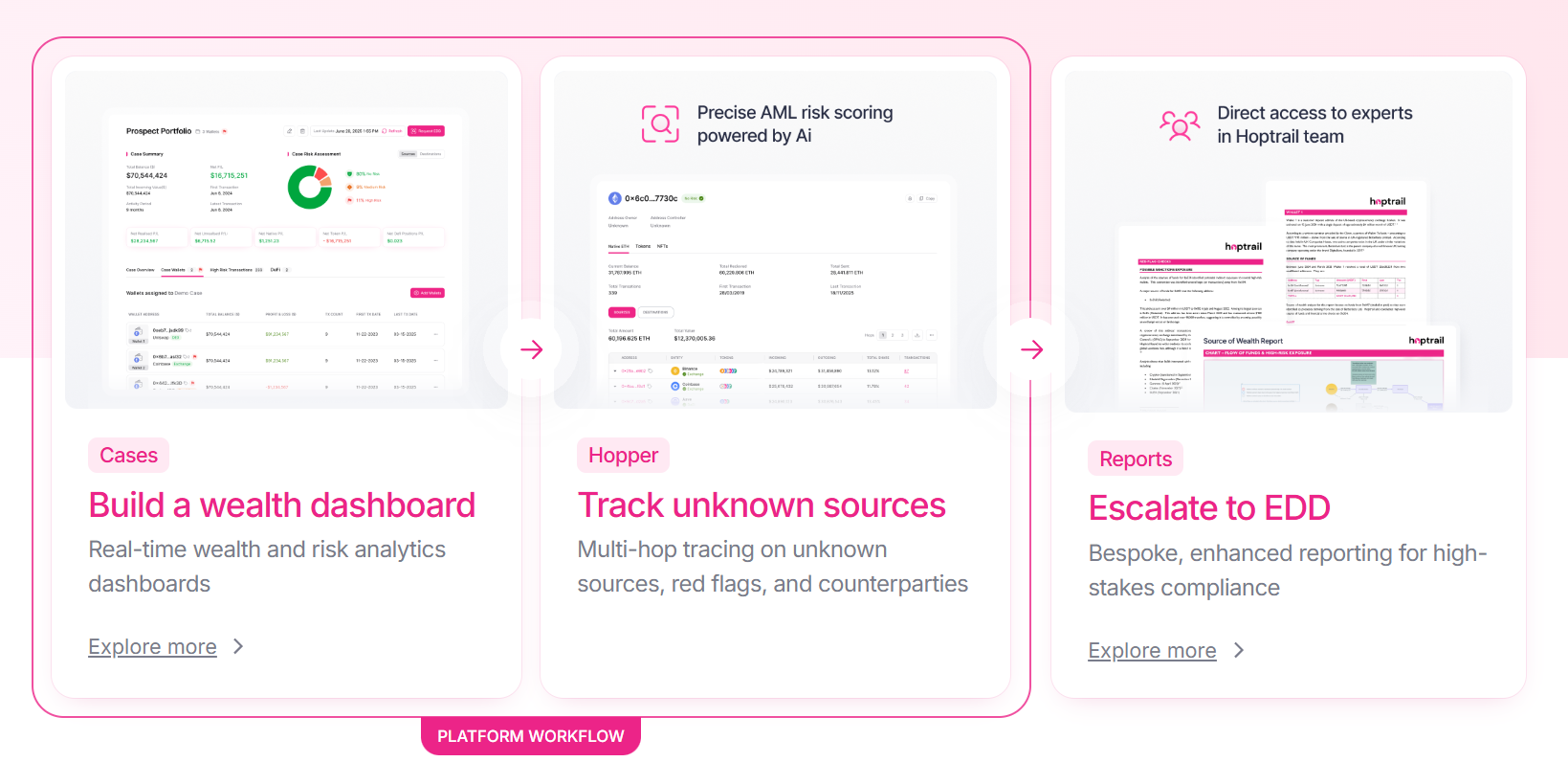
Hoptrail 2.0
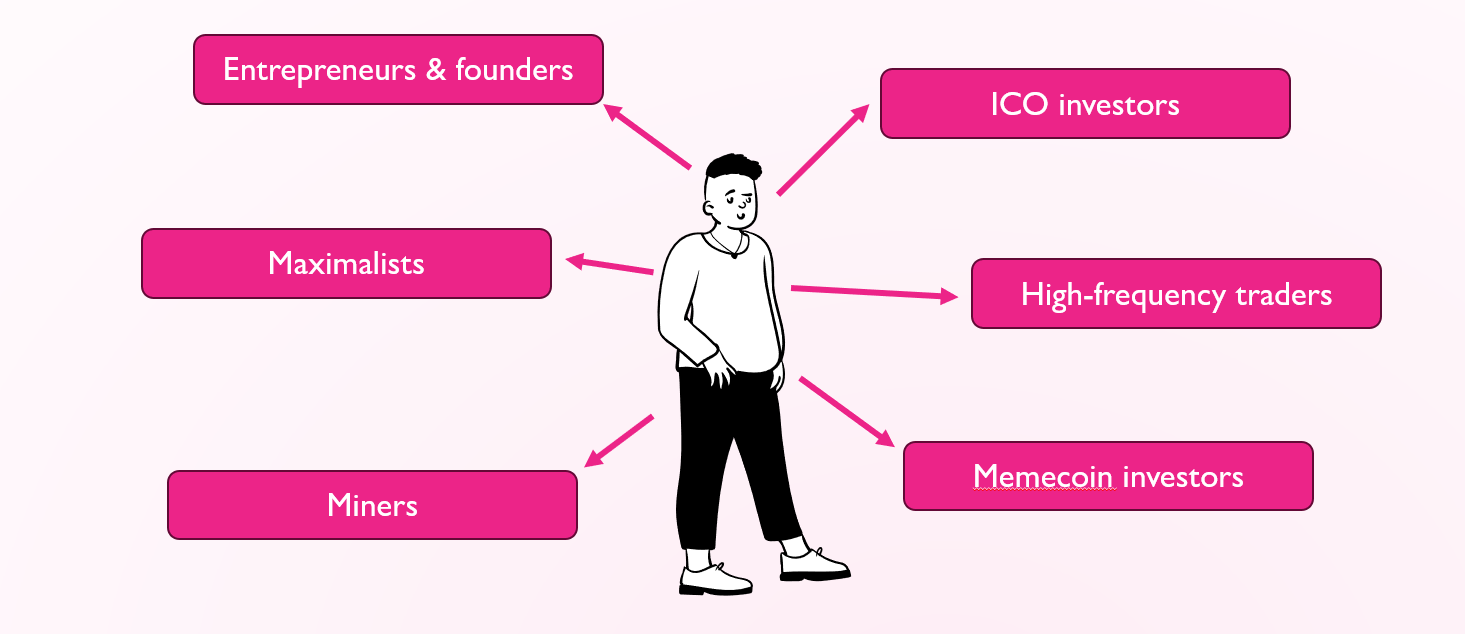
Crypto HNWIs: who they are and how they made their wealth
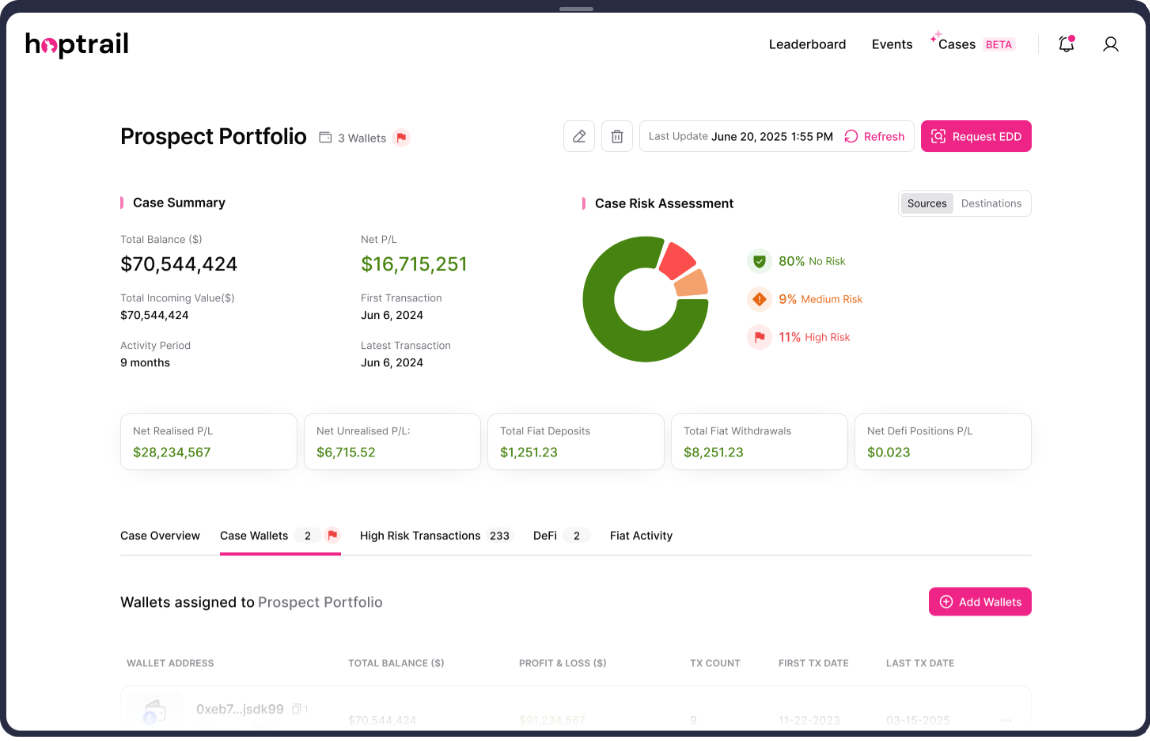
Cases: new source of wealth capabilities and upcoming features
Subscribe to the Hoptrail newsletter
Sign up with your email address to get the latest insights from our crypto experts.
